In recent times the importance of securing DATA is widely recognized as the direct connection between the data and revenue becomes more clear to organizations and individuals. So how do you secure your data??
Well, it starts by securing the host of the data and in this Article we will look into how to secure your Virtual Private Server (VPS).
We have identified 5 most essential security measures to take to ensure your VPS and data is secure
1. CHANGE THE DEFAULT SSH LOGIN METHOD #
SSH is the SECURE SHELL. This is a service that allows us to do remote connections computer-to-computer. In most cases when a VPS is provisioned, SSH logins and credentials are also provided.
If you use SSH to login to your VPS or have the service open just incase your GUI (Graphical User Interface) has an issue. Here is how to secure this service.
- CHANGE THE DEFAULT SSH USER
In most cases the default user is *root*.
Login in as root is not recommended, due to a couple of reasons, but the most important is that the user root is the default administrator, who can perform any administrative task which includes deleting other users and their files.
We, therefore, need to disable login as root.
1. Step one is to create another user. In this case, I call the user user1.
#useradd -m -d /home/user-home user1 –> Create the user
#passwd user1 –> Set password for user
2. Disable root login on SSH service configuration file.
The configuration file we will be editing is /etc/ssh/sshd_config.
Change the PermitRootLogin from yes to NO. If it is commented with a hash, remove the hash.
- CHANGE THE DEFAULT PORT
The default SSH port is 22. We need to change this to a not so obvious port. In this case port 10019.
We still edit the /etc/ssh/sshd_config.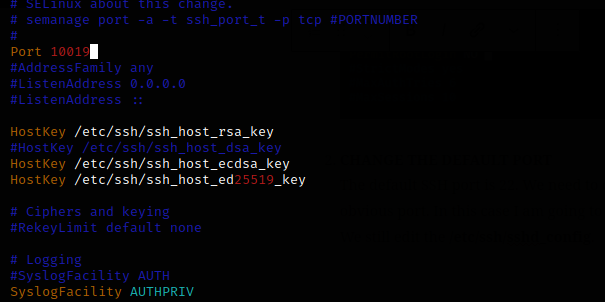
- Allow port through the firewall and restart the SSH service.
After the changes on the ssh configuration file, a restart of the SSH services (sshd/ssh) is required.
#systemctl restart sshd or #systemctl restart ssh
In most cases a default firewall is installed for most OS. For CentOS, Redhat and Fedora this firewall is firewalld. For Ubuntu the firewall is UFW.
You can always choose to disable the current firewall and install the one you are familiar with.
We need to allow the port through the firewall.
#firewall-cmd –permanent –allow-port=10019/udp
#firewall-cmd –permanent –allow-port=10019/tcp
#firewall-cmd –reload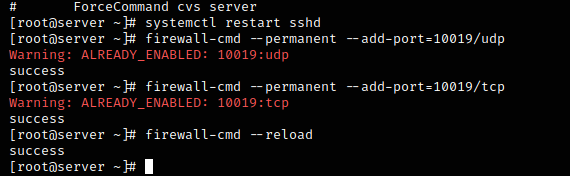
For better understanding, you can watch the following video.