Linux file permissions are a core part of system security and management, controlling who can read, write, or execute files. Understanding and managing these permissions is essential for every Linux administrator to keep systems secure and well-organized. Here’s a guide on Linux file permissions, the types of permissions, and how to configure them for optimal security.
1. Understanding the Basics of Linux File Permissions #
- Every file and directory in Linux has an associated set of permissions and ownership. Permissions define who can access or modify a file and what they can do with it. There are three key concepts:
- User (u): The owner of the file.
- Group (g): A group of users that may share access rights.
- Others (o): All other users on the system.
- Permissions are generally displayed as a combination of letters and numbers. For example:
-rwxr-xr--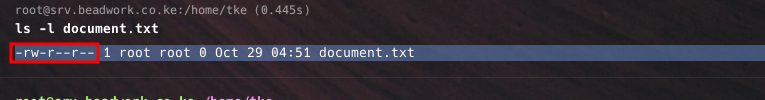
- This example includes 10 characters, where:
- The first character represents the file type (
-for files,dfor directories). - The next 9 characters are split into sets of three, representing permissions for the user, group, and others.
2. The Three Types of Permissions #
- Each permission set has three possible permissions:
- Read (r): Allows viewing the contents of a file or listing files in a directory.
- Write (w): Grants permission to modify the contents of a file or add/remove files in a directory.
- Execute (x): Permits executing a file as a program or script, or accessing files within a directory.
Using the example -rwxr-xr--, here’s how permissions apply:
| Section | Permissions | Details |
|---|---|---|
| User | rwx | Read, write, execute |
| Group | r-x | Read, execute |
| Others | r– | Read-only |
3. Using Numeric (Octal) Representation for Permissions #
- Permissions can also be represented by numbers:
- 4 for read (
r) - 2 for write (
w) - 1 for execute (
x)
- 4 for read (
- By summing these values, each permission set can be represented by a single digit. For instance:
7(4+2+1) gives read, write, execute.5(4+1) gives read, execute.4gives read-only.
The command chmod 755 filename applies rwxr-xr-x permissions. Here’s the breakdown:
| Permission Code | Result | Details |
|---|---|---|
| 7 | rwx | User has full permissions |
| 5 | r-x | Group can read and execute |
| 5 | r-x | Others can read and execute |
4. Setting Permissions with chmod #
chmodis the command used to change file permissions.- Below is the sysntax of the command
chmod [permissions] [filename]
- This command gives
rw-r--r--permissions: the owner can read and write, while others can only read. - Alternatively, permissions can be specified symbolically:
u: Userg: Groupo: Othersa: All (user, group, others)
- To add or remove permissions, use
+or-:
chmod u+x file.txt # Adds execute for user
chmod g-w file.txt # Removes write for group
chmod o+r file.txt # Adds read for others
5. Changing Ownership with chown #
- Each file and directory in Linux has an owner and group.
chownchanges file ownership. - Below is the sysntac of chown command
chown [owner][:group] [filename]chown tke file.txt # Changes owner to alice
chown tke:developers file.txt # Changes owner to alice and group to developers
6. Special Permissions: Setuid, Setgid, and Sticky Bit #
In addition to standard permissions, Linux offers special permissions for more control.
Setuid #
When applied to a file, Setuid (represented as an s in rws) allows users to run the file with the file owner’s permissions.
chmod u+s /path/to/file
Setgid #
Setgid (represented as an s in rwx) allows files created within a directory to inherit the group ID of the directory.
chmod g+s /path/to/directory
Sticky Bit #
The sticky bit (represented as a t in rwx) ensures only the file owner or root can delete or modify files in a directory.
chmod +t /path/to/directory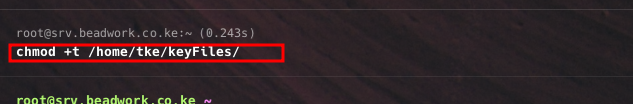
7. Examples of Common Permissions Configurations #
Here are a few real-world examples of permissions you might configure on your server:
- Private Files (644): For files like configuration files:
chmod 644 /etc/yourfile.conf- Executable Scripts (755): To allow only the owner to modify, but others to execute:
chmod 755 /usr/local/bin/script.sh- Secure Directories with Sticky Bit (1777): For shared directories where users can add files but cannot delete others’ files:
chmod 1777 /shared_directory8. Checking Permissions with ls -l #
- To view file permissions, use:
ls -l filename- You’ll see the full permission set and ownership:
-rwsr-Sr-- 1 tke wheel 0 Oct 29 04:51 document.txt
- In the above output;
-rwsr-Sr--represents permissions.tkeis the user (owner).wheelis the group.
9. Security Tips #
- Use Minimal Permissions: Only grant the permissions necessary for a file or directory to function.
- Avoid Setting Full Permissions (777): These allow unrestricted access, which can lead to security issues.
- Monitor Sensitive Files: Regularly audit permissions on sensitive files (e.g.,
/etc/passwd,/etc/shadow).
Linux file permissions are powerful tools for maintaining security and control. By understanding and carefully managing permissions, administrators can ensure only the necessary access is provided to files and directories, reducing the risk of unauthorized access.